Now we are gonna make another great protocol about switching : STP ( Spanning Tree Protocol )
WHAT IS STP ?
STP is a protocol that avoids loops within Layer – 2 communication. The algorithm of the protocol creates a non-loop network to us.

In the figure above, you can see two PCs and three switches. If PC-1 makes a broadcast, the traffic is flooded from all ports of the first switch and goes to switch 2 and switch 3. Switch-2 and 3 also floods that broadcast traffic from all its ports and a broadcast storm occurs.
STP blocks the redundant link that has no traffic on. So that there is no loop and broadcast storm occurs in the network. But how that guy does it ? 🙂
*Switches send BPDU packets to detect the loops in the network.
*BPDU are also used to select the root bridge in the network. Defaultly the oldest switch in the network is root.
*All switches find the best way to reach the “root bridge” and blocks the all other redundant links.
ROOT BRIDGE ELECTION
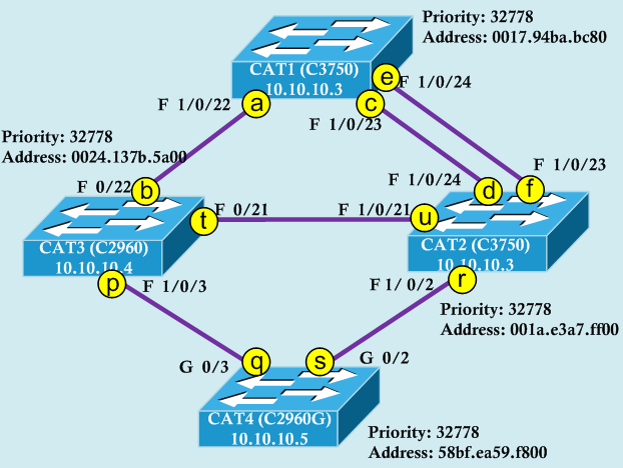
Let’s see how we can select the root bridge for spanning tree protocol. BPDU packets are send to the network each two seconds. Root bridge is the switch that has lowest Bridge ID ! Bridge id is the combination of the Priority ( which is a value between 0 – 61440, default 32768 ) and MAC address. The lowest bridge id is the root bridge in the network. That means lowest priority ( is checked first ) and lowest MAC address.

Can you determine which switch is root in this situation ?
- Lowest Bridge ID determines the root bridge (Bridge ID = Priority + MAC Address + Extended Sys. ID (To support VLAN for STP) )
- Default priority value = 32768
- Bridges use special data frames called BPDU to exchange information about bridge IDs and root path costs
- CAT1 is root bridge because of the lowest MAC address (Priority is equal)
STP PORT STATES
There are three STP port states ;
- Learning ( Takes 15 seconds, for BPDU )
- Listening ( Takes 15 seconds, to learn MAC-Addresses )
- Forwarding or Blocking